What is Inery DLS
Inery DLS (Distributed Ledger System) is an innovative data management solution that redefines ownership and control of data through its distributed and decentralized architecture. It provides enhanced security, scalability, and integrity, ensuring that all interactions are transparent, verifiable, and secure. By addressing key challenges of traditional data management, Inery DLS offers a reliable and cost-effective solution for various use cases, from enterprise-level applications to Global ecosystems.
How does Inery DLS Works
Inery DLS operates on a peer-to-peer (P2P) network, utilizing consensus mechanisms, cryptographic algorithms, and secure digital identity frameworks to provide a comprehensive data management system. It decentralizes data storage and access, giving data owners unprecedented control while ensuring that data is immutable and tamper-proof. With minimal integration costs, Inery DLS is a powerful tool for businesses looking to transition into a decentralized digital environment.
Distribution and Decentralization
The foundation of Inery DLS is its peer-to-peer (P2P) network, where nodes communicate directly with one another, ensuring that data is distributed evenly across the system. This decentralized approach eliminates single points of failure and provides unmatched data redundancy and availability.
P2P Network
Inery DLS leverages a peer-to-peer (P2P) network to facilitate seamless communication and data exchange between nodes. This decentralized network design enhances system resilience, ensures data availability, and distributes resources evenly across all participants. Within this P2P network, two types of nodes serve distinct yet complementary roles:
Direct Node Communication: Nodes within the P2P network communicate directly with each other, sharing data and state information without relying on a central authority. This decentralized communication path reduces latency and enhances data propagation across the network.
Dynamic Node Discovery: New nodes can dynamically join or leave the network, making Inery DLS adaptable to changing conditions. Node discovery and routing are handled using protocols like (Distributed Hash Table), ensuring efficient data lookups and minimizing communication overhead.
REST API Integration: The system nodes operates on a RESTful API interface that enables external applications and services to interact with Inery DLS nodes. This interface allows for seamless integration of data operations (read/write) with existing systems.
Secure Data Transmission: Data transmitted between nodes is encrypted using cryptographic techniques such as TLS/SSL, preventing eavesdropping and ensuring secure communication.
Multi-Channel Communication: Inery DLS supports multiple communication channels, including DLS RPC and WebSocket Connections, enabling real-time data synchronization and event-driven communication for applications requiring instant updates and notifications.
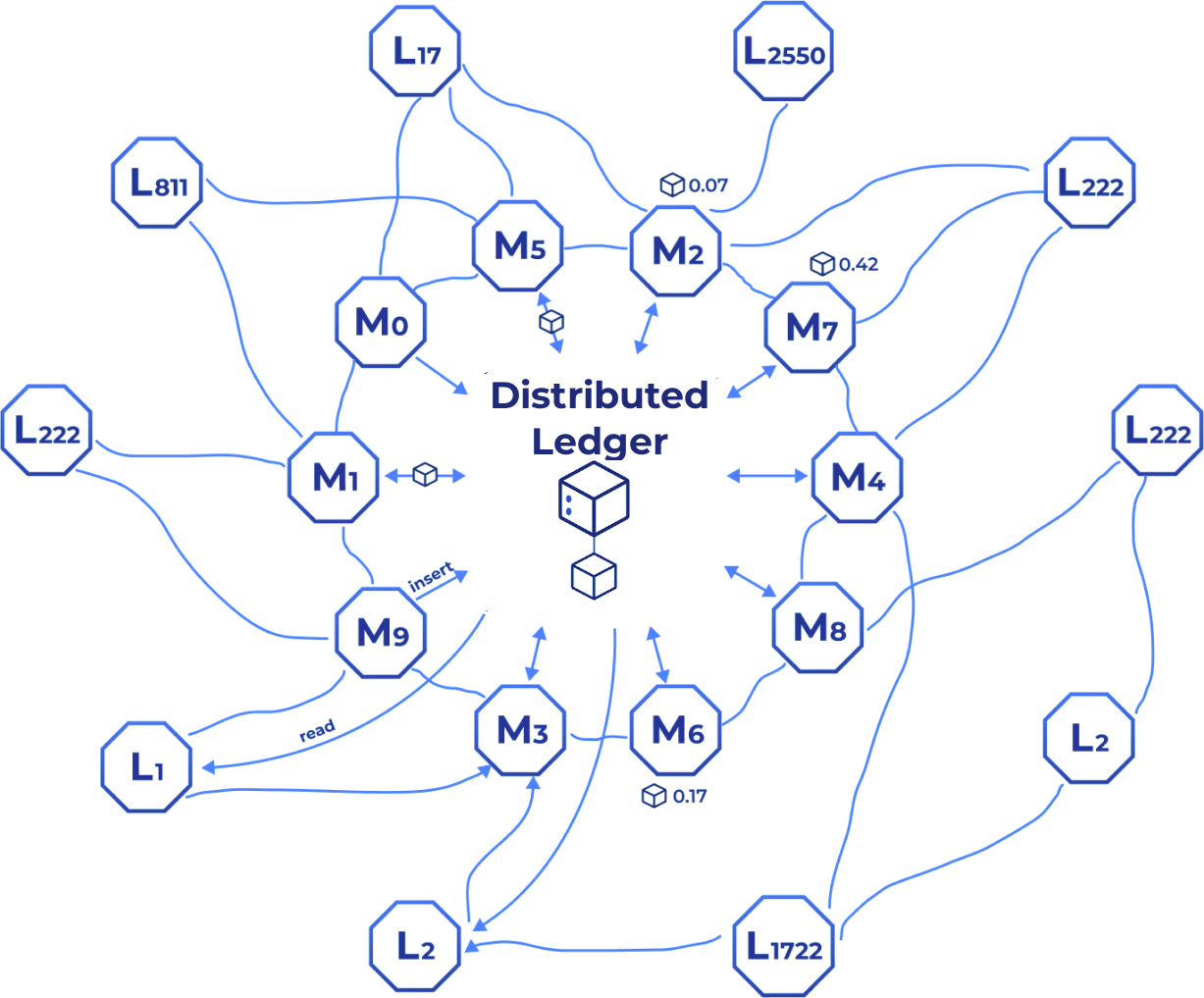
Master Nodes
Master Nodes are the backbone of the Inery DLS, responsible for maintaining the network's core functionalities. They play a crucial role in:
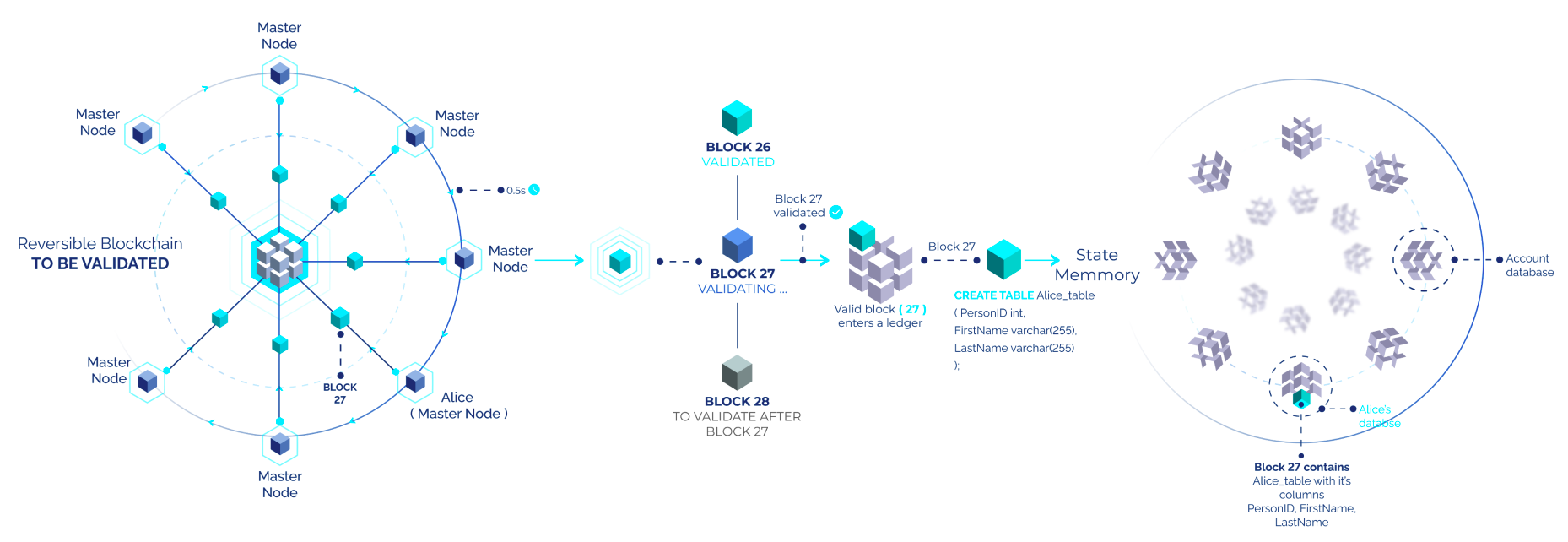
Transactions Validation: Master Nodes validate transactions, produce new blocks, and ensure data consistency across the network. By participating in the consensus process, they uphold the integrity and security of the entire system.
Network Maintenance: These nodes manage the network's overall health by performing critical maintenance tasks, such as preventing forks, managing node synchronization, and ensuring that all data is propagated accurately and efficiently.
Because of their crucial role in securing and maintaining the network, Master Nodes require more resources and computational power compared to Lite Nodes.
Lite Nodes
Lite Nodes contribute to the network’s scalability and accessibility by providing additional support for API consumption, data querying, and backup redundancy. They focus on the following areas:
API & Data Services: Lite Nodes serve as access points for external applications and services to interact with the Inery DLS. They handle REST API requests, process queries, and deliver real-time data updates without burdening the Master Nodes, ensuring smooth integration for developers and external systems.
Backup Redundancy & Resilience: Lite Nodes maintain copies of the blockchain data and provide backup redundancy, ensuring that data remains available even if certain nodes go offline. Their presence enhances network resilience and enables quick recovery in case of node failures or disruptions.
Scalability Enhancement: By offloading data requests and providing a bridge for applications to access the network, Lite Nodes enhance overall network scalability and performance. They allow the system to accommodate increased demand and traffic without compromising on speed or reliability.
Consensus Mechanism
Inery DLS employs a unique variant of the Delegated Proof-of-Stake (DPoS) consensus mechanism tailored to optimize performance, security, and data integrity. Unlike traditional DPoS models, Inery’s approach grants each master node equal authority, ensuring a balanced and decentralized decision-making process. The consensus is determined based on data parameters such as memory, bytes, and computational capacity, rather than tokens or assets.
Inery’s Delegated Proof-of-Equal-Stake (DPoES)
In this model, master nodes are selected to maintain the network’s integrity and validate transactions. Each master node holds an equal voting power in the consensus process, eliminating any potential influence imbalances and promoting fair participation.
Equal Authority for All Master Nodes: Every master node in the Inery network has the same level of authority, ensuring an even distribution of power and promoting trust and stability within the system.
2/3 Majority Consensus: For a transaction to be confirmed and a block to be produced, at least two-thirds of the master nodes must agree. This 2/3 majority rule prevents any minority group of nodes from disrupting or compromising the consensus, ensuring that decisions are collectively agreed upon by a significant portion of the network.
Asynchronous Byzantine Fault Tolerance (aBFT)
To complement its DPoS model, Inery incorporates Asynchronous Byzantine Fault Tolerance (aBFT) for enhanced fault tolerance and network resilience. aBFT allows nodes to achieve consensus even when some nodes may be unresponsive or exhibit faulty behavior.
Resilient to Faulty Nodes: aBFT enables the network to reach consensus even if up to one-third of the master nodes are compromised or offline. This ensures that the network continues to function securely and reliably under challenging conditions.
Low Latency & Fast Finality: aBFT’s asynchronous design minimizes waiting times for message exchanges, leading to faster transaction finality and low-latency communication between nodes.
Encryption Algorithms and Cryptographic Concepts
Security is ensured through advanced cryptographic algorithms like AES-256 for data encryption and SHA-256 for data integrity verification. This means that all data stored and transmitted within the Inery DLS network is protected from unauthorized access, ensuring confidentiality and compliance with global data protection standards.
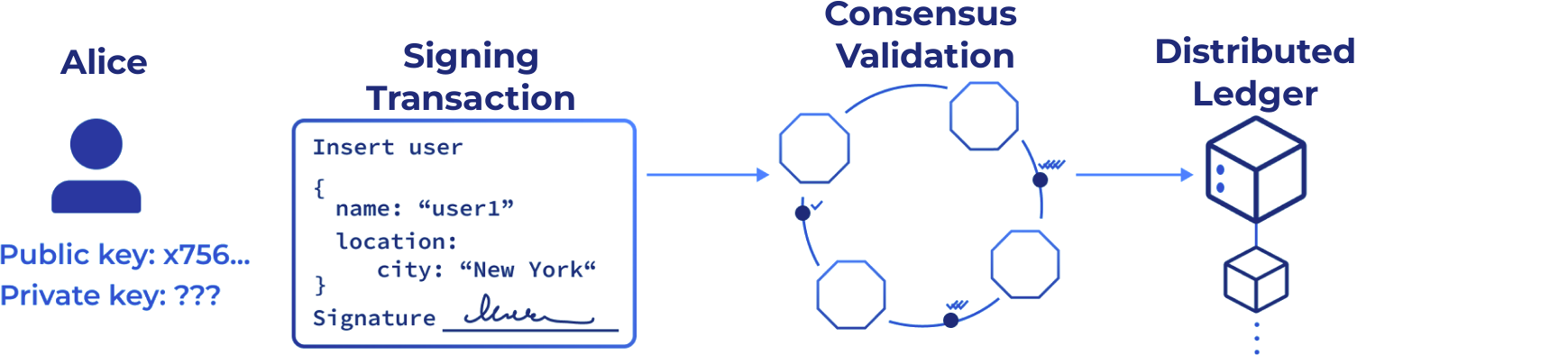
Digital Signatures and Verification
Digital signatures ensure the authenticity and integrity of data by verifying the sender's identity. Every transaction in Inery DLS is digitally signed, making it tamper-proof and verifiable by all network participants. This mechanism guarantees non-repudiation, ensuring that actions cannot be denied after execution.
Elliptic Curve Digital Signature Algorithm (ECDSA)
ECDSA is used to generate digital signatures for every transaction within the network, ensuring that only the rightful owners can authorize data operations.The elliptic curve-based algorithm offers stronger security with smaller key sizes, resulting in faster processing and lower resource consumption compared to traditional RSA-based signatures.
SHA-256 (Secure Hash Algorithm 256-bit)
SHA-256 is used to create unique cryptographic hashes for data stored and processed within the system. This ensures data integrity by providing a unique digital fingerprint for each transaction. Any attempt to alter the data would produce a completely different hash, making unauthorized modifications easily detectable.
Data Encryption in Transit and at Rest:
All data is encrypted both in transit and at rest using a combination of symmetric (AES-256) and asymmetric encryption techniques (RSA or ECC). This dual-layered encryption strategy ensures end-to-end security, making sure that data is protected from eavesdropping, tampering, and unauthorized access throughout its lifecycle.
RSA (Rivest-Shamir-Adleman) Algorithm
Inery DLS utilizes RSA for securely transmitting encryption keys across the network. RSA is an asymmetric encryption technique that uses a pair of keys: a public key for encryption and a private key for decryption. This process ensures that sensitive data, such as encryption keys, are securely exchanged between nodes without exposing them to unauthorized entities.
AES-256 (Advanced Encryption Standard 256-bit)
AES-256 is employed for encrypting data both at rest and in transit, protecting sensitive information from unauthorized access. This symmetric encryption algorithm is highly resistant to cryptographic attacks, ensuring that even if data is intercepted, it remains incomprehensible without the appropriate decryption key.
Digital Identity & Access Control
Inery DLS incorporates a robust Digital Identity Management framework, utilizing Public Key Infrastructure (PKI) for secure identity verification. Access controls are enforced using Role-Based Access Control (RBAC) and Attribute-Based Access Control (ABAC) models, allowing for granular permissions and ensuring that data interactions are only accessible to authorized entities.

Public Key Infrastructure (PKI)
PKI is utilized for managing digital certificates and public/private key pairs, enabling secure communications and identity verification across the network. This ensures that entities interacting within Inery DLS are legitimate and authorized to access specific resources or perform operations.
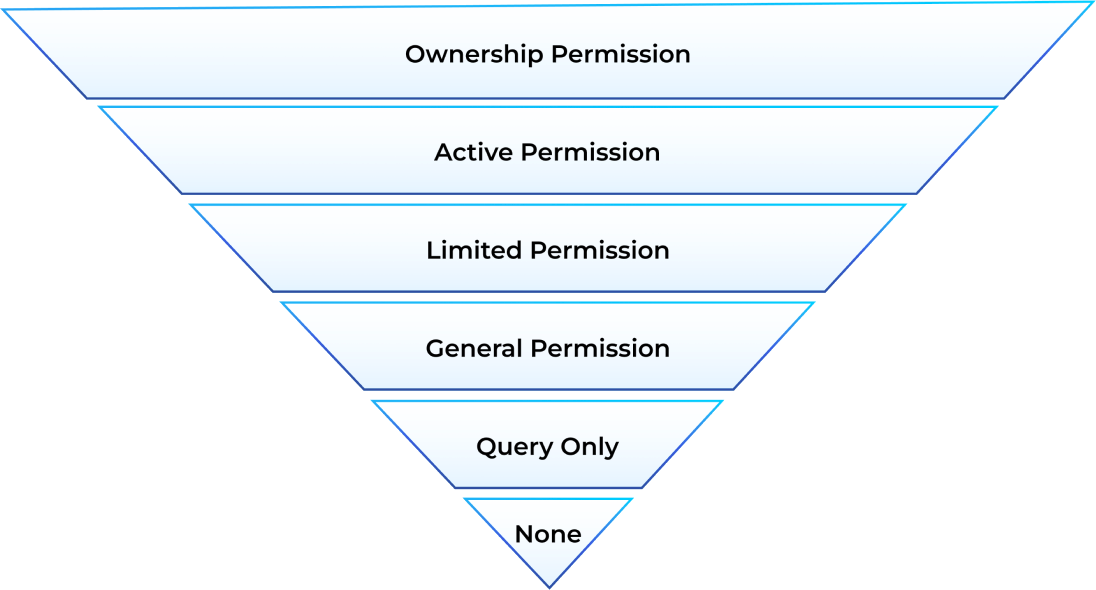
Hierarchical Permission Structure
Permissions in Inery DLS are managed through a hierarchical schema, where each permission level is defined with a specific authority and scope. At the top of this hierarchy is the Owner Permission, which acts as the root authority for managing all subordinate permissions. The owner permission can create, modify, or revoke other permissions, giving it complete control over the entity’s operations within the network
Owner Permission: The root-level permission that has the ultimate authority over the account and its subordinate permissions. It can delegate specific authorities to other permissions and serves as the highest level of control within the hierarchical structure.
Active Permission: A mid-level permission used for day-to-day operations, such as executing transactions and managing resources. This permission is typically controlled by a separate private key and is granted by the owner to enhance security and compartmentalize authority.
- Custom Permissions: Permissions created for specific actions or operations, such as issuing smart contracts, managing digital identities, or updating database records. Each custom permission is associated with its own private key, which must be used to sign transactions requiring that specific authority.
Multi-Signature Transactions
Multi-signature (multisig) capability allows multiple parties to jointly authorize a single transaction. This feature is critical for applications requiring enhanced security, such as financial transactions or organizational decision-making processes, ensuring that no single entity can act unilaterally without consensus.
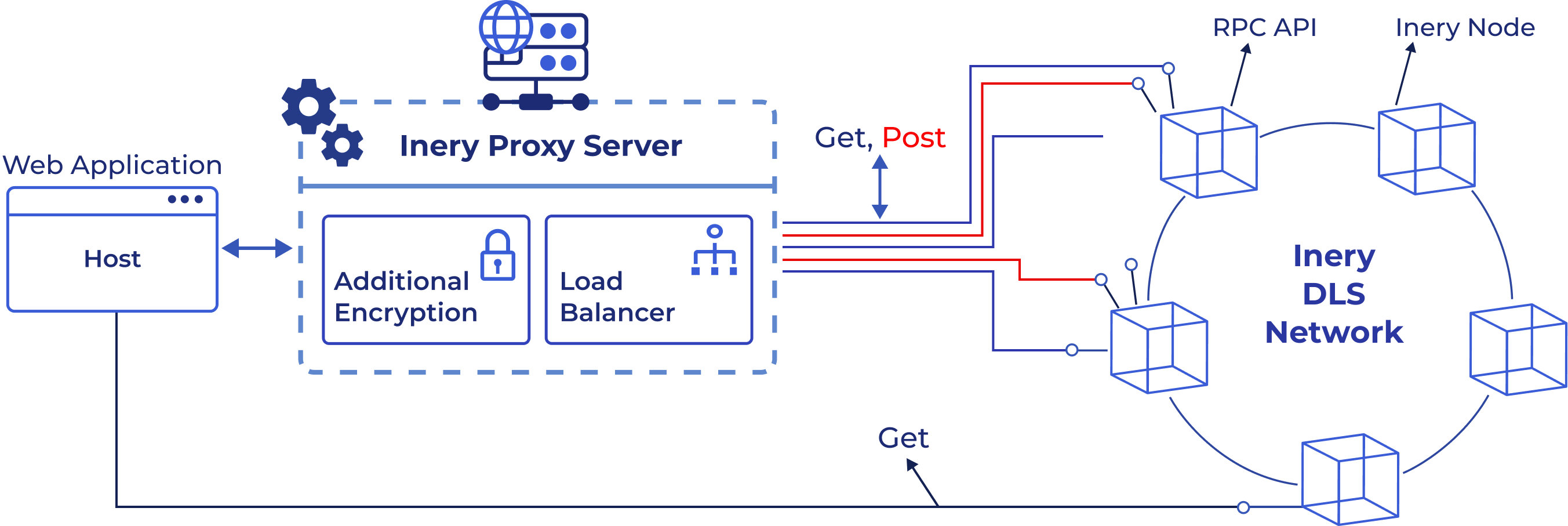
Inery API's and Communication Protocols
Inery DLS offers a versatile API system designed to facilitate seamless communication and integration. Each Inery DLS node comes with an RPC API plugin, enabling direct interaction with the database core through secure SSH connections. Additionally, Inery provides libraries in various programming languages, making it easy to communicate across different protocols.
IneryDB features its own set of APIs, hosted on a proxy server, that include advanced functionalities such as digital signature generation, additional entry encryption, and P2P load balancing. These APIs are also used by IneryGUI for database management and interactions.
For real-time data monitoring, Inery has developed WebSocket (WS) protocols that operate independently. These protocols can be implemented as plugins on any node, allowing live streaming of DLS transactions and database status updates.
For more details, see Inery DLS API's.